How It Works
Sof Scanner works by executing opensource security scanners in your pipeline / environment then logging those results to a tracking server.
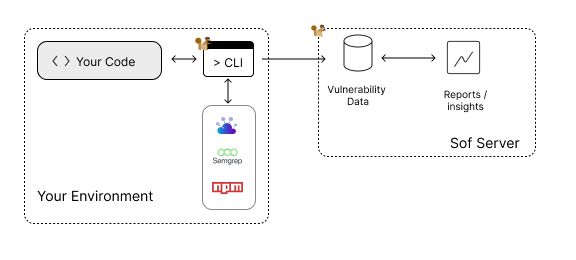
The CLI Tool
The CLI tool is the first part of SOF Scanner. It is a NPM application that executes security scanners on your source code. During the execution it also captures the effected code so you have a clear reference of where the security issue lives. It is also able to scan and categorize vulnerabilities to several 'components', with a component being a discrete part of your code. This enables mono-repo scanning as you can now easily segment your vulnerabilities to subsystems and services.
The Server
The server is the second part of SFO Scanner. It captures vulnerabilities and fingerprints them. This fingerprint is important as it creates a way for you to track when a vulnerability is first discovered, when it is resolved and if it is regressed. Fingerprints are bound to Project/Component domains.
How we thinking about relationships
SOF Scanner is designed to follow the CI/CD process and focused around complex teams and projects. As such the general hierarchy of information is:
- Projects - the highest order object, a project represents a collection of components, runs and vulnerabilities
- Components - a component is a subsection of a project and a unique way to track / filter vulnerabilities to subsystems.
- Runs - A run is a unique scan of the code. Ideally this matches your pipeline runid so you can trace and follow the run to the issues. This sits at the project level.
- Vulnerabilities - Each project has vulnerabilities. Vulnerabilities are then associated to runs and components via the fingerprint. This enables a historical and timeline based understanding of how a vulnerability lives in your code.